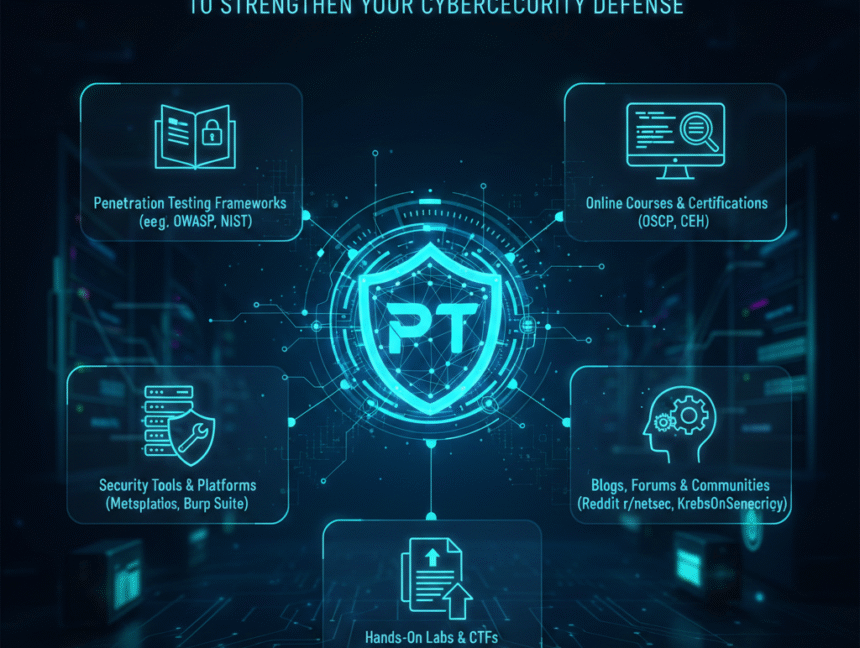
Top Penetration Testing Resources to Strengthen Your Cybersecurity Defense
The Ultimate Pen Testing Tools Cheat Sheet For Cybersecurity Penetration testing (also known as pen-testing) is the process of scanning a computer network, application, or system for exploitable vulnerabilities. Vulnerabilities are gaps or weaknesses in your security that could be leveraged by malicious hackers to compromise your systems. Hackers use penetration testing techniques to hack