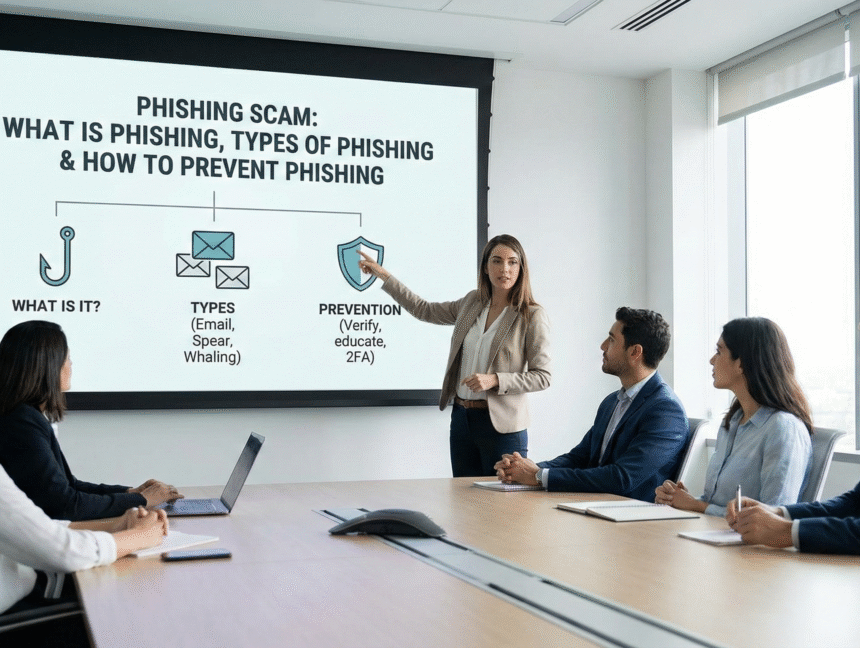
Phishing Scam: What is Phishing, Types of Phishing & How to prevent Phishing
The term phishing is derived from the word fishing, referring to attackers “casting a bait” in the hope that users will take the bite. Cybercriminals attempt to trick individuals into sharing sensitive information such as credit card numbers, bank details, usernames, passwords, or other valuable data by using fake yet legitimate-looking emails, websites, advertisements, or messages.