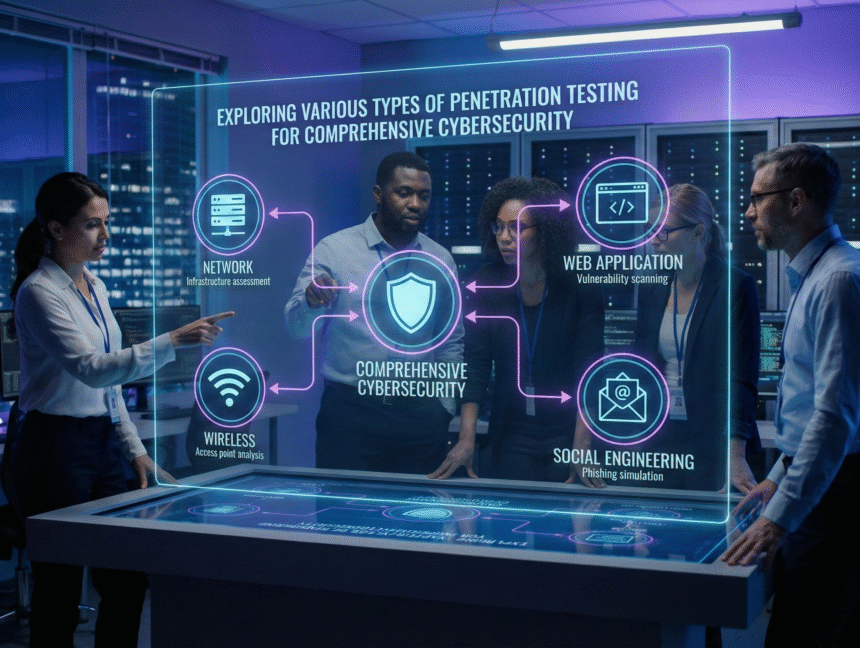
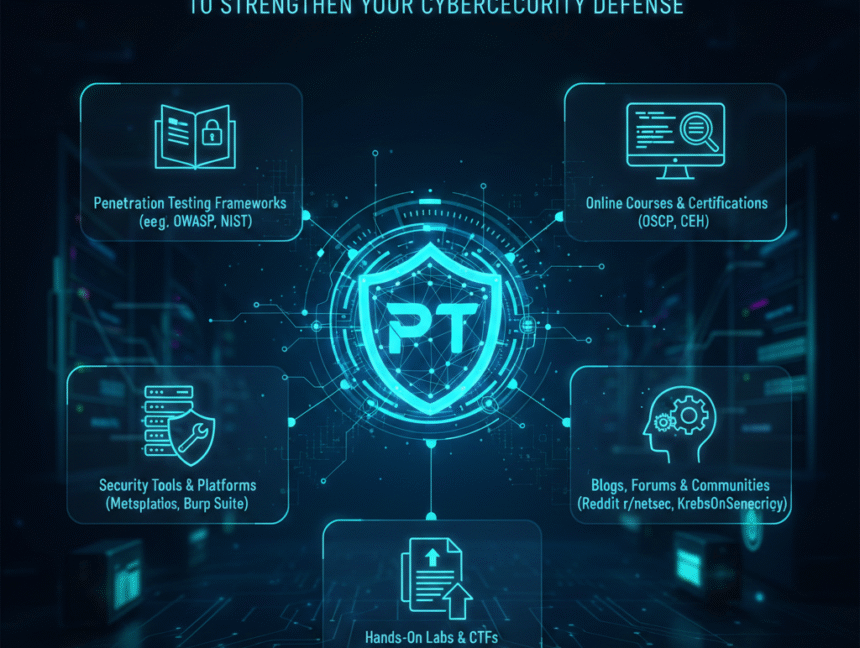
Safeguard Your Business with Cyber Security Hive’s Top-Rated Penetration Testing Services in India
In today’s digital era, web applications play a critical role in the operations of modern businesses across India. However, these applications are also prime targets for cybercriminals who continually develop new techniques to exploit vulnerabilities.